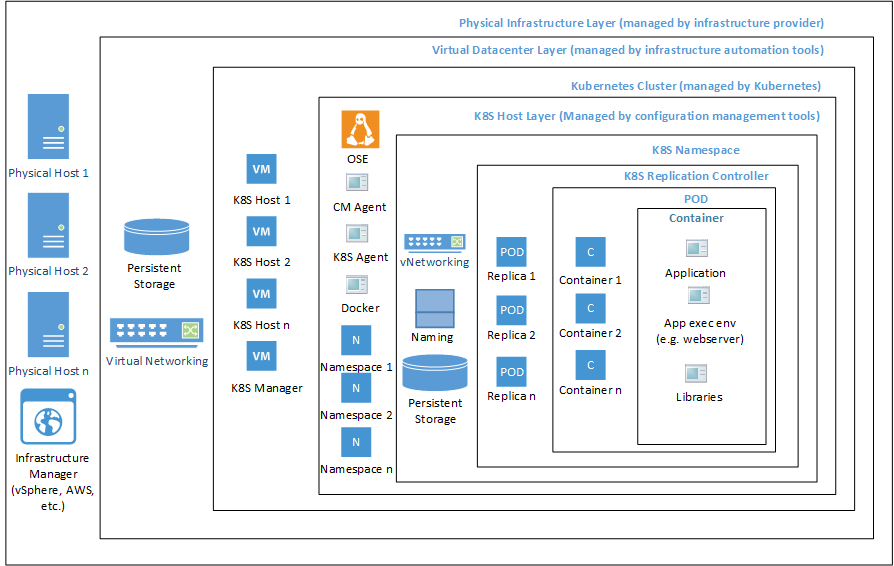
First, here is a quick intro to namespaces. Note that namespaces and cgroups are orthogonal by design.
- Historical discussions
https://lwn.net/Articles/219794/ (2007)
https://lwn.net/Articles/531114/ (2013)
- Modern descriptions:
https://jvns.ca/blog/2016/10/10/what-even-is-a-container/, and then newer discussion on network namespaces on linux: https://blog.scottlowe.org/2013/09/04/introducing-linux-network-namespaces/
"Each network namespace is a logically a separate networking stack, with separate addresses, separate firewall rules, separate qos policies etc.
This has nothing to do with systemd etc.
in this picture we created 3 pairs
https://etherarp.net/network-isolation-of-services-with-systemd/
https://lwn.net/Articles/219794/ (2007)
https://lwn.net/Articles/531114/ (2013)
- Modern descriptions:
https://jvns.ca/blog/2016/10/10/what-even-is-a-container/, and then newer discussion on network namespaces on linux: https://blog.scottlowe.org/2013/09/04/introducing-linux-network-namespaces/
"Each network namespace is a logically a separate networking stack, with separate addresses, separate firewall rules, separate qos policies etc.
Network devices and sockets belong to a particular network namespace and everything else figures out which network namespace you are talking about from the socket or network device."
This has nothing to do with systemd etc.
in this picture we created 3 pairs
- ns1_veth0, globalns_veth1 (1st pair)
- ns2_veth0, globalns_veth2 (2nd pair)
- ns1_veth1, ns2_veth1 (3rd pair)
Originally all pairs exist in the default/global namespace, and we can assign them to different namespaces so that the picture looks like this:
https://etherarp.net/network-isolation-of-services-with-systemd/